Over six billion SIM cards power mobile connections worldwide, quietly enabling secure communication across continents. Most people see a SIM card as just a tiny chip, yet it holds the keys to your digital identity and personal data. Understanding how SIM cards work reveals the hidden systems that connect devices, protect user information, and support everyday activities like calls, texts, and international travel.
Key Takeaways
| Point | Details |
|---|---|
| Core Functions of SIM Cards | SIM cards authenticate users, manage data, and control network access, playing a vital role in mobile connectivity. |
| Evolution of SIM Technology | SIM cards have advanced from physical formats to eSIMs and iSIMs, enhancing flexibility and integration in mobile devices. |
| Data Storage Capabilities | SIM cards store critical information such as unique identifiers and service details, with modern cards supporting extensive contact storage. |
| Security Measures | SIM cards utilize advanced encryption and authentication protocols to ensure the security and privacy of mobile communications. |
What SIM Cards Are and Their Core Functions
A Subscriber Identity Module (SIM) card is a small, sophisticated piece of technology that serves as the digital passport for mobile communication. According to research from Wikipedia, these integrated circuit cards contain a microcontroller and non-volatile memory designed to securely store critical subscriber information. Think of a SIM card like a digital identity card for your mobile device.
The core functions of a SIM card extend far beyond simple storage. At its heart, a SIM card performs three critical tasks:
- Network Authentication: Stores the International Mobile Subscriber Identity (IMSI) and authentication key (K₁)
- User Data Management: Securely stores personal contacts, SMS messages, and service-related information
- Network Access Control: Provides a unique identifier that allows mobile devices to connect to cellular networks
As mobile technology evolves, SIM cards have transformed from traditional removable cards to more advanced embedded SIM (eSIM) and integrated SIM (iSIM) technologies. According to recent research from arXiv, these modern iterations maintain the core principle of tying subscriber identity to hardware while offering more flexible provisioning capabilities. Whether physical or digital, the fundamental purpose remains the same: providing a secure, portable method of identifying and authenticating mobile subscribers across global networks.
Read more about travel SIM card options to understand how these tiny technological marvels keep us connected worldwide.
Types of SIM Cards and Key Differences
Mobile technology has dramatically evolved, transforming SIM card designs from simple removable chips to sophisticated digital identifiers. According to research from arXiv, we can now categorize SIM cards into three primary generations: physical SIMs, embedded SIMs (eSIMs), and integrated SIMs (iSIMs), each representing a significant leap in mobile connectivity technology.
Let’s break down the key characteristics of these SIM card types:
Here’s a comparison of the main types of SIM cards:
| Type of SIM | Physical SIM | eSIM | iSIM |
|---|---|---|---|
| Form Factor | Removable card | Soldered chip | Integrated chip |
| Installation | Manual | Remote/digital | Manufacturer only |
| Profile Flexibility | Single or dual | Multiple profiles | Multiple profiles |
| Provisioning | Swap card | QR code/OTA | Device firmware |
| Use Cases | Most mobiles | Phones Wearables |
IoT devices Smartphones |
| Durability | Susceptible to damage | Less physical risk | Highly robust |
Physical SIM Cards:
- Removable plastic card with a chip
- Requires manual insertion and removal
- Limited storage and profile flexibility
Embedded SIMs (eSIMs):
- Soldered directly onto device motherboard
- Multiple digital profiles can be stored
- Remote provisioning enables instant plan switching
- Learn more about travel eSIM options for international connectivity
As highlighted by Wikipedia, eSIMs offer remarkable advantages like reduced physical damage risk and enhanced flexibility for travelers. The newest innovation, integrated SIMs (iSIMs), takes this further by embedding SIM functionality directly into the device’s system-on-chip, promising even greater miniaturization and seamless connectivity. These technological progressions demonstrate how mobile identity solutions continue to prioritize security, convenience, and user experience.

Data Storage: What SIM Cards Hold
SIM cards are more than just tiny chips; they’re compact digital vaults storing critical mobile communication information. According to Wikipedia, these small devices pack an impressive amount of data, including unique identifiers and network-specific details that enable seamless mobile connectivity.
Here’s a breakdown of the key data stored on SIM cards:
Unique Identifiers:
- ICCID (Integrated Circuit Card Identifier)
- IMSI (International Mobile Subscriber Identity)
- Authentication Key (Kᵢ)
Network and Service Information:
- Local Area Identity (LAI)
- Service Provider Name (SPN)
- Service Dialing Numbers (SDN)
- Short Message Service Center (SMSC) number
Research from Encyclopedia.pub reveals that SIM card storage capacity has dramatically evolved, ranging from 8 KB to 256 KB.
Early SIM cards could store around 20 contacts and a few messages, but modern SIMs can now hold over 250 contacts, plus complex network roaming preferences. Explore how international data works with travel SIM cards to understand the practical implications of these storage capabilities.
Beyond basic storage, SIM cards also include value-added service applications and advice-of-charge parameters, making them sophisticated tools for managing mobile communication and personal connectivity. These tiny technological marvels continue to evolve, offering increasingly complex and secure methods of storing and protecting our digital mobile identities.
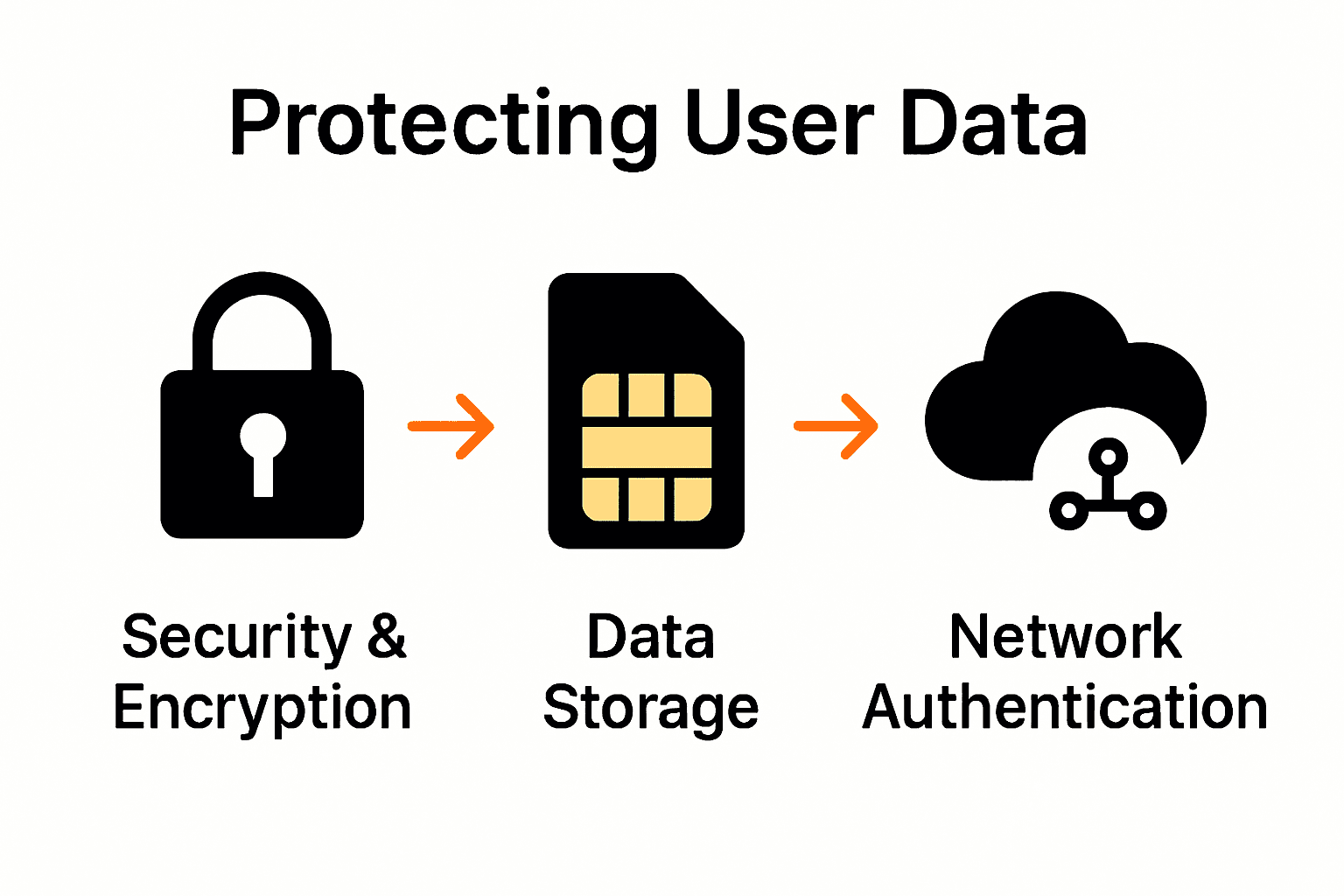
How SIM Card Security and Encryption Work
Security is the cornerstone of SIM card technology, transforming these tiny chips into robust digital guardians of mobile communication. Research from Kaspersky reveals the ongoing evolution of encryption methods to protect user data and prevent potential security breaches.
Key Security Mechanisms:
- Encryption Algorithms: Advanced encryption standards like 3DES and AES
- Key Management: Secure generation and storage of cryptographic keys
- Authentication Protocols: Verifying user and device identity
The global mobile industry has continuously adapted to emerging threats. A notable example came from Security Research Labs, which exposed vulnerabilities in older DES encryption methods, prompting mobile operators to implement more sophisticated security measures. Learn more about modern mobile security techniques to understand these technological advancements.
According to the GSMA, SIM cards now serve as trusted secure elements, particularly in Internet of Things (IoT) applications. They encrypt uplink data and verify downlink commands through sophisticated key management infrastructure, effectively eliminating the need for separate security solutions. This multi-layered approach ensures that your mobile communication remains private, secure, and protected from potential cyber threats.
Common Myths and Mistakes About SIM Data
Navigating the world of SIM technology can be tricky, with numerous misconceptions clouding understanding of how these digital identity chips actually work. According to research from SimOptions, many widespread beliefs about SIM cards and eSIMs are far from reality.
Top SIM Data Myths Debunked:
-
Myth: eSIMs are expensive
- Reality: They often reduce production and distribution costs
-
Myth: eSIMs make users more trackable
- Reality: Device IMEI determines traceability, not SIM type
-
Myth: eSIM activation requires store visits
- Reality: Completely digital activation via QR codes
One persistent misconception is that eSIMs are limited in functionality. Learn more about mobile data flexibility to understand the nuanced capabilities of modern SIM technology. In fact, contemporary eSIMs can store multiple carrier profiles, enabling users to switch plans seamlessly without physical SIM swapping.
The digital evolution of SIM technology continues to challenge traditional assumptions. Modern eSIMs offer enhanced convenience, security, and flexibility, dismantling outdated notions about mobile connectivity. By understanding these technological advancements, users can make more informed decisions about their mobile communication needs.
Keep Your Data Safe and Travel Connected with Trusted SIM Solutions
Worried about how your personal information and mobile identity are stored and protected when travelling? The article on how SIM cards store data highlights common questions about security, reliability, and ease of use, especially as many travellers move between locations and rely on their phones for everything. Understanding the difference between traditional SIMs, eSIMs, and how data is securely kept can make all the difference when choosing the right solution for your next trip.
At SimCorner.com, we offer expertly curated SIM cards and travel connectivity products that put your mind at ease. You benefit from safe, secure, and flexible data options that work wherever you are in the world. Avoid technical headaches, protect your digital identity, and get the seamless support you need on the road. Visit our main site to discover the travel SIM that suits you, read more about your choices on our blog, and take the smart step to stay protected and connected now.
Frequently Asked Questions
What is a SIM card and how does it work?
A SIM card, or Subscriber Identity Module, is a small chip that securely stores subscriber information, enabling mobile devices to authenticate and connect to cellular networks.
What types of data can be stored on a SIM card?
SIM cards can store unique identifiers (like ICCID and IMSI), network and service information, and personal data such as contacts and SMS messages, enhancing mobile communication.
How do eSIMs differ from traditional SIM cards?
Unlike traditional physical SIM cards, eSIMs are soldered directly onto the device and can store multiple profiles, allowing for remote provisioning and easier plan management without physical swapping.
What security measures are in place to protect SIM card data?
SIM cards utilize encryption algorithms, secure key management, and authentication protocols to protect user data and ensure secure mobile communication, especially in IoT applications.
Recommended
- Instructions pour installer une carte SIM à l’étranger facilement Oct-202
- 7 Proven Ways to Choose the Best International Travel SIM Card Oct-2025
- Instructions pour installer une carte SIM à l’étranger facilement Oct-2025



